Why I made this guide
For the better part of the last 3 months, my primary web server has been under moderate brute force bot attack. I only just realized it was a brute force bot attack 2 weeks ago when I noticed in the logs for one of my client’s WordPress sites, there was 600 login attempts in the past 24 hours. Funny thing is the only reason I was even looking at the logs was because my server had been seizing up at 100% CPU and memory utilization repeatedly over the past few months.
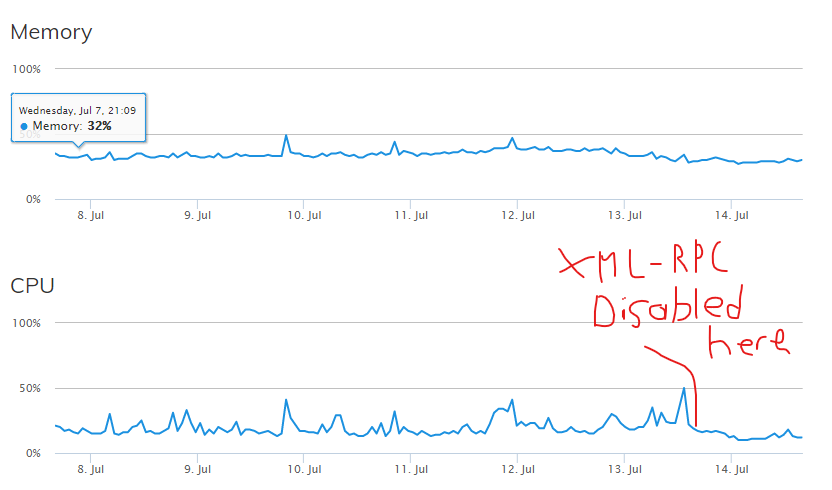
This past 2 weeks has been a learning lesson but I thought I’d share what I’ve done for all of my client sites to harden their security defenses. What’s more, I can even show you the exact instant that I disabled XML-RPC for all my client’s sites on my server and the effect it had on my server’s CPU utilization. Even the memory consumption has dropped 5% or 200 MB.
1) Keep WordPress, themes, and plugins updated regularly
I can feel your collective eye roll in reading this and yes I know… It’s palpable. If you don’t have a regular reminder meaning every 2 weeks to log into your WordPress sites and update them, then perhaps you’re not heeding my advice fully. Keeping WordPress, themes, and plugins updated doesn’t mean checking it every 3 months, it means bi-weekly or even weekly.
2) Delete plugins you aren't using
No point in having a plugins installed that you’re not using. More plugins installed just means more potential threat vectors.
3) Don't use a plugin when a little PHP code will do the trick
Want to create some additional image sizes, just throw in some PHP code into your child theme’s functions.php file instead of installing an entire plugin to do it.
4) Ensure that your wp-config.php file permissions are set to 600
For the love of all that is holy and good, please double check the file permissions on your wp-config.php file. When I’ve taken over some client sites, I’ve seen it set to 644 for some inexplicable reason. It might be a pain to get your FTP/SFTP credentials and punch them into FileZilla, but believe me, a little pain now is better than a lot of pain trying to remediate a database breach.
If you don’t know how to do this, here’s a simple tutorial on how to do so. Just remember, you ONLY changing the file permissions for the wp-config.php file, nothing else.
5) Use a brute force WordPress plugin to limit login attempts
If you’ve ever used cPanel Installatron wizard to install WordPress, you’ll see that in the option configuration page, you can have it automatically “Limit Login Attempts.” You’ll need a plugin to limit the number of login attempts any particular IP address may have in a given time frame.
Personally, I’ve been using Loginizer and I’ve been very happy with it but Limit Login Attempts Reloaded has a great reputation as well.
6) Change the WoredPress admin login URL so bots can't even find the login page in the first place
If you’ve ever used cPanel Installatron wizard to install WordPress, you’ll see that in the option configuration page, you can have it automatically “Limit Login Attempts.” You’ll need a plugin to limit the number of login attempts any particular IP address may have in a given time frame.
Personally, I’ve been using Loginizer and I’ve been very happy with it but Limit Login Attempts Reloaded has a great reputation as well.
7) Disable WordPress XML-RPC entirely
XML-RPC is a Remote Procedure Call method that uses XML passed via HTTP as a transport. It was originally designed to allow the WordPress mobile app to access your WordPress backend from your phone. It was a cool idea when it was around but it’s become another chink in the armor that bots love to attack.
If you have NOT disabled XML-RPC just yet and have Loginizer installed and are under attack, you can see just how many times the bots are hitting your xmlrpc.php file. Time to get that fixed. Scott Brown wrote a superb article on how to tackle this. I went with option two and just added the following code to my .htaccess file.
# disable xmlrpc
<FilesMatch "^xmlrpc\.php$">
Require all denied
8) Check for any suspicious or old user accounts and delete them
If your database has been compromised due to improper file permissions, then your opponents have likely already created administrator user accounts on your WordPress installation. If they have, be sure to delete them. This is also a good time to ensure that there aren’t any former employees or contractors with logins. If so, you know what to do with them.
9) Use strong passwords for your WordPress, cPanel, SFTP, and SSH logins.
I don’t feel like this one requires much of an introduction but triple check that you’re using complex passwords for each layer in your web server stack.
Summary
While this isn’t an exhaustive list, it’s a great start to cover the majority of threat vectors. For the paranoid, a more thorough guide can be found at Malcare’s blog here.